Network Security in the Internet of Things (IoT) Era
DOI:
https://doi.org/10.5281/zenodo.12789562ARK:
https://n2t.net/ark:/40704/JIEAS.v2n4a06References:
24Keywords:
internet of Things (IoT), Network Security, Lightweight Cryptography, Blockchain Technology, Machine Learning, Fog Computing, Cyber Threats, Heterogeneous Devices, Resource Constraints, Scalability, Real-Time Protection, Privacy Concerns, IoT Security Challenges, innovative Security Solutions, IoT NetworksAbstract
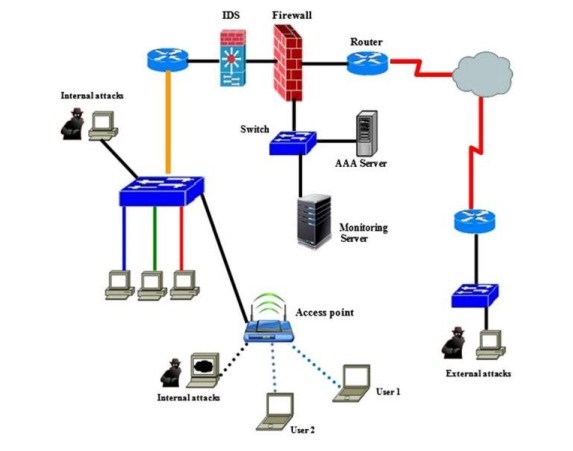
The Internet of Things (IoT) represents a significant transformation in how devices communicate and interact, offering unprecedented convenience and efficiency. However, this interconnected environment also introduces substantial security challenges. Traditional network security measures are often inadequate for IoT environments due to their unique characteristics, such as resource constraints and diverse device types. This paper explores the current state of network security in the IoT era, examines the specific challenges posed by IoT environments, and presents innovative solutions and best practices for securing IoT networks. Through comprehensive analysis and experimental data, we demonstrate the effectiveness of these solutions in mitigating security risks associated with IoT.
Specifically, we investigate the implementation of lightweight cryptography for resource-constrained devices, the use of blockchain technology for secure and decentralized authentication, the application of machine learning algorithms for anomaly detection, and the integration of fog computing to enhance real-time security services. Experimental results indicate significant improvements in security posture and performance, validating the proposed methodologies as viable solutions for IoT security challenges.
Downloads
Metrics
References
Alaba, F. A., Othman, M., Hashem, I. A. T., & Alotaibi, F. (2017). Internet of Things security: A survey. Journal of Network and Computer Applications, 88, 10-28.
Amaral, L. A., de Lima, L. F., de Oliveira, M. V., & Braga, R. A. (2018). Machine learning algorithms to detect cyber attacks in IoT systems. International Journal of Computer Science and Information Security, 16(5), 18-27.
Buchmann, J., Dahmen, E., & Hülsing, A. (2014). XMSS - A practical forward secure signature scheme based on minimal security assumptions. Post-Quantum Cryptography, 117-129.
Chiang, M., & Zhang, T. (2016). Fog and IoT: An overview of research opportunities. IEEE Internet of Things Journal, 3(6), 854-864.
Dorri, A., Kanhere, S. S., Jurdak, R., & Gauravaram, P. (2017). Blockchain for IoT security and privacy: The case study of a smart home. IEEE PerCom Workshops.
Roman, R., Zhou, J., & Lopez, J. (2013). On the features and challenges of security and privacy in distributed Internet of Things. Computer Networks, 57(10), 2266.
Liu, T., Cai, Q., Xu, C., Zhou, Z., Ni, F., Qiao, Y., & Yang, T. (2024). Rumor Detection with a novel graph neural network approach. arXiv Preprint arXiv:2403. 16206.
Liu, T., Cai, Q., Xu, C., Zhou, Z., Xiong, J., Qiao, Y., & Yang, T. (2024). Image Captioning in news report scenario. arXiv Preprint arXiv:2403. 16209.
Xu, C., Qiao, Y., Zhou, Z., Ni, F., & Xiong, J. (2024a). Accelerating Semi-Asynchronous Federated Learning. arXiv Preprint arXiv:2402. 10991.
Zhou, J., Liang, Z., Fang, Y., & Zhou, Z. (2024). Exploring Public Response to ChatGPT with Sentiment Analysis and Knowledge Mapping. IEEE Access.
Zhou, Z., Xu, C., Qiao, Y., Xiong, J., & Yu, J. (2024). Enhancing Equipment Health Prediction with Enhanced SMOTE-KNN. Journal of Industrial Engineering and Applied Science, 2(2), 13–20.
Zhou, Z., Xu, C., Qiao, Y., Ni, F., & Xiong, J. (2024). An Analysis of the Application of Machine Learning in Network Security. Journal of Industrial Engineering and Applied Science, 2(2), 5–12.
Zhou, Z. (2024). ADVANCES IN ARTIFICIAL INTELLIGENCE-DRIVEN COMPUTER VISION: COMPARISON AND ANALYSIS OF SEVERAL VISUALIZATION TOOLS.
Xu, C., Qiao, Y., Zhou, Z., Ni, F., & Xiong, J. (2024b). Enhancing Convergence in Federated Learning: A Contribution-Aware Asynchronous Approach. Computer Life, 12(1), 1–4.
Wang, L., Xiao, W., & Ye, S. (2019). Dynamic Multi-label Learning with Multiple New Labels. Image and Graphics: 10th International Conference, ICIG 2019, Beijing, China, August 23--25, 2019, Proceedings, Part III 10, 421–431. Springer.
Wang, L., Fang, W., & Du, Y. (2024). Load Balancing Strategies in Heterogeneous Environments. Journal of Computer Technology and Applied Mathematics, 1(2), 10–18.
Wang, L. (2024). Low-Latency, High-Throughput Load Balancing Algorithms. Journal of Computer Technology and Applied Mathematics, 1(2), 1–9.
Wang, L. (2024). Network Load Balancing Strategies and Their Implications for Business Continuity. Academic Journal of Sociology and Management, 2(4), 8–13.
Li, W. (2024). The Impact of Apple’s Digital Design on Its Success: An Analysis of Interaction and Interface Design. Academic Journal of Sociology and Management, 2(4), 14–19.
Wu, R., Zhang, T., & Xu, F. (2024). Cross-Market Arbitrage Strategies Based on Deep Learning. Academic Journal of Sociology and Management, 2(4), 20–26.
Wu, R. (2024). Leveraging Deep Learning Techniques in High-Frequency Trading: Computational Opportunities and Mathematical Challenges. Academic Journal of Sociology and Management, 2(4), 27–34.
Wang, L. (2024). The Impact of Network Load Balancing on Organizational Efficiency and Managerial Decision-Making in Digital Enterprises. Academic Journal of Sociology and Management, 2(4), 41–48.
Chen, Q., & Wang, L. (2024). Social Response and Management of Cybersecurity Incidents. Academic Journal of Sociology and Management, 2(4), 49–56.
Song, C. (2024). Optimizing Management Strategies for Enhanced Performance and Energy Efficiency in Modern Computing Systems. Academic Journal of Sociology and Management, 2(4), 57–64.
Downloads
Published
How to Cite
Issue
Section
ARK
License
Copyright (c) 2024 The author retains copyright and grants the journal the right of first publication.

This work is licensed under a Creative Commons Attribution 4.0 International License.
















