Trojan Virus Detection and Classification Based on Graph Convolutional Neural Network Algorithm
DOI:
https://doi.org/10.70393/6a69656173.323735ARK:
https://n2t.net/ark:/40704/JIEAS.v3n2a01Disciplines:
Computer ScienceSubjects:
CybersecurityReferences:
1Keywords:
Trojan Virus, Graph Convolutional Neural Network, Virus Detection and ClassificationAbstract
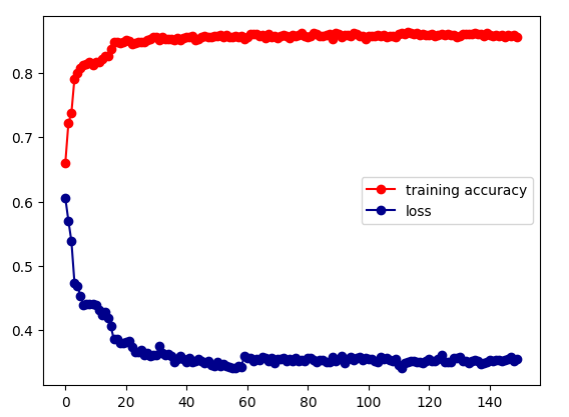
This article proposes a new method for Trojan virus detection and classification based on graph convolutional neural network (GCN) algorithm. By observing the performance evaluation indicators of the model during the training process, the accuracy of the model continued to improve from the initial 64.27% to 88.28% and gradually stabilized, proving that the model can effectively identify Trojan viruses during the training process. In addition, confusion matrix analysis based on the training set shows that the model performs quite well in classification tasks, with an overall accuracy of 91.06%, precision of 89.24, recall of 92.63, and F1 score of 90.91. These indicators indicate that the model can demonstrate good performance in detecting Trojan viruses from various perspectives. On the test set, the model also demonstrated excellent performance, with an accuracy rate of 90.96%, an accuracy rate of 90%, a recall rate of 91.43%, and an F1 score of 90.71. By analyzing the confusion matrix of the test dataset, it can be seen that the classification performance of the model in practical applications is similar to that on the training set, further verifying its good generalization ability. In summary, the experimental results in this article demonstrate that the Trojan virus detection method based on graph convolutional neural networks has high accuracy and stability, and demonstrates superior performance compared to traditional detection methods. This method provides new ideas and technical support for Trojan virus detection in the field of network security, which can effectively respond to increasingly complex network security threats and provide theoretical basis and practical guidance for related research and applications. Through further optimization and improvement, the method proposed in this article is expected to play a greater role in future Trojan virus detection, helping to enhance the level of network security protection.
Downloads
Metrics
Published
Versions
- 2025-07-27 (2)
- 2025-04-01 (1)
How to Cite
Issue
Section
ARK
License
Copyright (c) 2025 The author retains copyright and grants the journal the right of first publication.

This work is licensed under a Creative Commons Attribution 4.0 International License.
















